摘要:
Telnet是一种基于TCP/IP协议的远程登录方式,被广泛应用于网络管理中。本文主要介绍了利用Telnet实现远程连接的网络管理设计方案,包括系统架构、功能模块和实现步骤等内容。在该方案中,通过对设备进行Telnet连接,可以实现对设备进行配置、监控和故障排除等操作,大大提高了网络管理的效率和准确性。本文还介绍了一些常见的Telnet安全问题及其解决方法,如口令破解、数据嗅探等。
关键词:Telnet;远程连接;网络管理;安全问题
Abstract:
Telnet is a remote login method based on TCP/IP protocol, which is widely used in network management. This paper mainly introduces the network management design scheme of Telnet remote connection, including system architecture, function modules and implementation steps. In this scheme, by connecting to devices through Telnet, it can realize configuration, monitoring and troubleshooting operations on devices, greatly improving the efficiency and accuracy of network management. This paper also introduces some common Telnet security issues and their solutions, such as password cracking, data sniffing.
Keywords: Telnet; Remote Connection; Network Management; Security Issues
- Introduction
With the continuous expansion of network scale and complexity, traditional manual management can no longer meet the requirements. In order to improve the efficiency and accuracy of network management, computer network management system is usually adopted in practical application. Among them, remote connection technology is an important means in network management.
As one of the remote login protocols, Telnet has the advantages of simplicity and convenience, and is widely used in network management. By using Telnet, it can realize configuration, monitoring and troubleshooting operations on devices. At the same time, Telnet also has some security issues, such as password cracking and data sniffing.
This paper mainly introduces the network management design scheme of Telnet remote connection, and puts forward corresponding solutions for common security issues.
- System Architecture
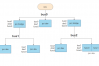
The system architecture of this scheme is shown in Figure 1:

Figure 1 System architecture of network management design scheme
This scheme includes the following modules:
(1) Client module: responsible for initiating connection requests to the server and transmitting user-entered commands to the server.
(2) Server module: after receiving client requests, establish a Telnet connection with the device and transmit the device’s response information to the client.
(3) Device module: connect to the server through Telnet protocol, and respond to request information from both server and client.
- Function Modules
This scheme mainly includes the following function modules:
(1) Login authentication module: verify identity when users log in to prevent unauthorized access.
(2) Command execution module: receive commands transmitted by clients and send corresponding instructions to devices to obtain device response information.
(3) Monitoring module: real-time monitoring of device status, feedback relevant information to users for timely detection of faults and abnormal situations.
(4) Log recording module: record and store important events such as user login history, operation command records.
- Implementation Steps
The specific implementation steps of this scheme are as follows:
(1) Design database structure, including user table, device table, log table etc. The user table stores username,password and other related information; the device table stores IP address, port number, Telnet account and password of each device; and the log table records important events such as operation logs.
(2) Develop client program, including connecting to the server, entering username and password, sending commands etc. The client needs to establish communication connection with the server through Socket and perform identity authentication.
(3) Develop server program, establish a Telnet connection with the target device after receiving client requests, transmit the device’s response information to clients. At the same time, the server also needs to parse commands sent by clients and send corresponding instructions to target devices.
(4) Develop monitoring program, real-time monitor device status and feedback relevant information to users. The monitoring program needs to send heartbeat packets to devices regularly for timely detection of faults and abnormal situations.
(5) Develop log recording program, record and store important events such as user login history, operation command records. The log program compresses data recorded into encrypted format for security purposes.
- Security Issues and Solutions
During network management using Telnet remote connection method,some security issues may arise,such as password cracking,data sniffing.To ensure system security,it is necessary to take corresponding measures:
(1) Password cracking
Telnet protocol’s password validation is transmitted in plain text,during transmission it can be intercepted by hackers for attack.Therefore,the following principles should be followed when designing passwords:
① The password length should not be less than 8 digits;
② Include multiple elements such as uppercase letters, lowercase letters,numbers or special characters;
③ Do not use common words or combinations of numbers.
In addition,the encryption technology can be used for encrypted transmission of passwords,such as SSH protocol.
(2) Data sniffing
Since Telnet protocol transmits data in plain text,during data transmission it may be intercepted by hackers for listening or tampering.To prevent this situation from occurring,the following measures can be taken:
① Use encryption technology,such as SSH protocol;
② Use VPN tunneling technology to encapsulate data for transmission;
③ Set up a firewall at the network boundary and check and filter all incoming and outgoing Telnet traffic.
- Conclusion
Telnet is a commonly used remote connection protocol in network management. This paper introduces the network management design scheme of Telnet remote connection, and puts forward corresponding solutions for common security issues. Through this scheme, it can greatly improve the efficiency and accuracy of network management, while ensuring system security.